6
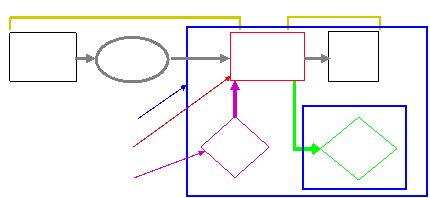
The Access Control Model
Object
Resource
Reference
monitor
Guard
Do
operation
Request
Principal
Source
Authorization
Audit log
Authentication
Policy
1. Isolation boundary
2. Access control
3. Policy
1.Isolation
Boundary to prevent attacks outside access-controlled
channels
2.Access
Control for channel traffic
3.Policy
management