7
Isolation
Attacks on:
Program
Isolation
Policy
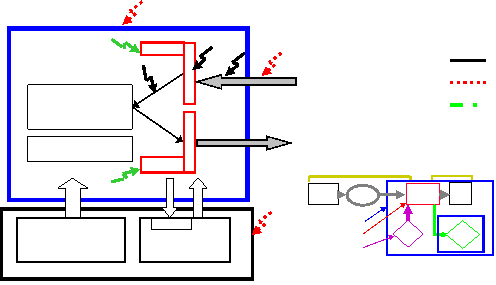
Services
Boundary Creator
G
U
A
R
D
G
U
A
R
D
policy
policy
Program
Data
guard
Host
I am isolated if anything that
goes wrong is my fault
Actually, my programs fault
Object
Resource
Reference
monitor
Guard
Do
operation
Request
Principal
Source
Authorization
Audit log
Authentication
Policy
1. Isolation boundary
2. Access control
3. Policy