8



Access Control Mechanisms:
The Gold Standard
The Gold Standard
·Authenticate principals: Who made a request
-Mainly people, but also channels, servers, programs
(encryption implements channels, so key is a principal)
(encryption implements channels, so key is a principal)
·Authorize access: Who is trusted with a resource
-Group principals or resources, to simplify management
- Can define by a property, e.g. “type-safe” or “safe for scripting”
·Audit: Who did what when?
•Lock = Authenticate + Authorize
•Deter =
Authenticate + Audit
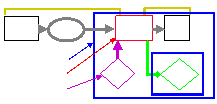
Object
Resource
Reference
monitor
Guard
Do
operation
Request
Principal
Source
Authorization
Audit log
Authentication
Policy
1. Isolation boundary
2. Access control
3. Policy